Cloud Computing Security
- Cloud Software as a Service (SaaS): In this service model, the consumer uses the provider’s applications on a cloud infrastructure. The consumer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, storage, or even individual application capabilities. However, the consumer might have access to limited user-specific application configuration settings.
- Cloud Platform as a Service (PaaS): This service model allows the consumer to deploy consumer-created or acquired applications onto the cloud infrastructure, using programming languages and tools supported by the provider. The consumer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, or storage, but controls deployed applications and possibly application-hosting environment configurations.
- Cloud Infrastructure as a Service (IaaS): This service model allows the consumer to provision processing, storage, networks, and other fundamental computing resources. The consumer is hence able to deploy and run arbitrary software, which an include operating systems and applications. The consumer does not manage or control the underlying cloud infrastructure, but controls operating systems, storage and deployed applications.
Let us see an example of the PaaS cloud service model with the help of a diagram (shown below). In this example, Demo Bank is a cloud user (consumer) and his vendor (cloud service provider) is ABC. ABC is providing PaaS (Platform as a Service) to Demo Bank and Demo Bank has deployed his application (http://public.demobank.com) on an ABC server called CCServer. Here, Demo Bank doesn’t have to worry about the infrastructure cost and maintenance, and has control over the deployed application and possibly application-hosting environment configurations. Eventually, a Demo Bank client accesses the http://public.demobank.com application as if the application is hosted by Demo Bank itself.
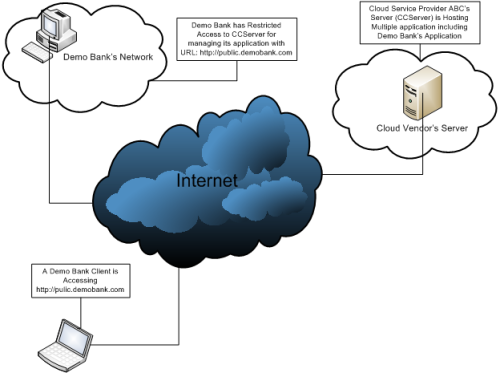
Diagram: Example of PaaS - Demo Bank Using PaaS cloud service provided by ABC
Now we know what cloud computing is, but why do we need cloud computing? Well, the answer is simple - it facilitates deployment of applications without the cost and complexity of buying and managing the underlying hardware and software layers.
However, due to security issues, the benefits of cloud computing are not being reaped to their fullest. Some of the important security issues are:
- In cloud computing, a single server hosts multiple applications of different users. Now, if any of the applications hosted on the server is vulnerable, it might lead to compromise or unavailability of other applications as well.
- Since a variety of applications are hosted on a single server, it is very likely that a large number of ports are open on the server, thus widening the network-level attack surface. If any of the services running on these ports are vulnerable, the server can be compromised.
- Many cloud vendors use virtual machines to run different OS instances on a single hardware platform for serving multiple users, which opens up a new attack vector. These virtual machines have multiple flaws that can be exploited in order to compromise the server
- If an application with critical data is hosted on cloud, all sensitive and critical information remain with the cloud service provider and there is always a threat of theft of company proprietary information by the cloud provider itself.
- Due to lack of transparency, auditing is very difficult and at times not possible in cloud computing. If something goes wrong with your application or there is a possibility of unauthorized access, it would be very difficult to conduct forensic investigations in cloud environment.
- It is difficult to ensure the integrity of computational results of an application in a cloud environment.
- It is difficult to enforce the enterprise authentication and authorization framework in cloud.
- Identify the asset for the cloud deployment: Identify wherever it is possible to shift only part of the application functions to the cloud rather than the complete application and data. Evaluate the criticality of these assets and the corresponding impact on business in case of unavailability of these assets due to whatsoever reason.
- Take Back Authentication Control: Most of the time, the authentication mechanism used for accessing (for management, administration, or usage) cloud application is too weak. This results in a breach, in which case, taking the authentication control back from the cloud service provider is a good option. Obviously, it reduces some of the benefits of the cloud, but it allows you to use strong authentication mechanisms and implement the company standard password policy, etc.
- Data storage and segregation: Typically the data in the cloud is in a shared environment, which is why it is important to find out what is done to segregate data at rest. The cloud provider should provide evidence that encryption schemes were designed and tested by experienced specialists.
- Transparency: Data owners wish to audit how their data is being handled at the cloud, and in particular, ensure that their data is not being abused or leaked, or at least have an unalterable audit trail when it does happen. Hence, ensure that the cloud vendor provides enough transparency.
- Choose Appropriate Cloud Deployment Model: Regardless of the service model utilized (SaaS, PaaS, or IaaS), there are four deployment models for cloud services. The appropriate cloud deployment model is selected depending on the criticality of the asset and specific requirements. Different cloud deployment models are:
- Public Cloud: The cloud infrastructure is owned by an organization selling cloud services and is made available to the general public or a large industry group.
- Private Cloud: The cloud infrastructure is operated solely for a single organization. It may be managed by the organization or a third party, and may exist on premises or off premises.
- Community Cloud: The cloud infrastructure is shared by several organizations having similar requirements. Since the cloud infrastructure is shared among fewer organizations, it provides a higher level of security and privacy in comparison with public clouds. Community cloud may be managed by the organizations or a third party, and may exist on premises or off premises.
- Hybrid Cloud: The cloud infrastructure is a composition of two or more clouds (private, community, or public). The objective of hybrid cloud is to provide the local data benefits of the private clouds with the economies, scalability, and on-demand access of the public cloud.
- Security Guidance for Critical Areas of Focus in Cloud Computing V2.1 - For Service and Deployment models
In : Security
Tags: cloud computing securiy models
